Crypto Custody: An Institutional Primer
This report was created by CCData’s award winning research team, commissioned by Zodia Custody.
This report, Crypto Custody: An Institutional Primer, was created by CCData’s award winning research team, commissioned by Zodia Custody. The report provides readers with an impartial overview of the digital asset custody landscape, highlighting the crucial role that custodians play in this evolving sector. It also explores the intricacies of digital asset custody, common challenges encountered by institutions, factors for institutional integration, and current trends in the industry.
Digital Asset Custody: Who, what and why?
Digital assets present a transformative opportunity for the financial sector, with the industry reaching an estimated valuation of $3tn in 2021. However, despite the increased adoption of this new asset class, the unique characteristics of digital assets pose considerable risks and challenges for institutions, especially when it comes to the safeguarding and transacting of these assets.
The challenges associated with the custody of digital assets are unique when compared to those found in the traditional finance sector - ranging from the loss or theft of private keys to exchange vulnerabilities and regulatory uncertainties - as such, it is vital that institutions have the proper infrastructure in place to confidently interact with these novel markets.
Over time, the shortfalls associated with self-custody have become increasingly evident for institutions looking to navigate these novel markets, especially when considering the trading and operational needs of these firms. Challenges arise from operational intricacies, security concerns, and availability of insurance policies, among others. As a result, institutions should only deal with regulated custodians to securely and confidently navigate digital asset markets.
This report aims to shed light on the crucial role of custody in the digital asset space, with an emphasis on the institutional custody landscape. The analysis covers the significance of digital asset custody, security measures adopted, key considerations in selecting a custody provider, insights into varied custody models, and a review of the latest trends and advancements in the field.
Defining Custody within Digital Assets
Over the last decade, digital assets have seen substantial growth, evolving from financial outliers to a central topic of global debate. While the sector has matured significantly in this time, and the institutionalisation of the industry continues, there are still significant risks to consider when navigating the space - with the safekeeping and storing of digital assets being one of the largest barriers to entry, especially at an institutional level.
According to Fidelity’s Institutional Digital Assets Study, 35% of respondents identified security concerns as a key obstacle to investment, whilst 26% expressed concerns surrounding private key management. As such, digital asset custodians play a pivotal role in the sector, helping safeguard and ease the security risks associated with holding digital assets.
Investment managers have fiduciary obligations to effectively mitigate counterparty risk and ensure regulatory compliance. As a result, digital asset custodians are essential to further the adoption of cryptocurrencies and reduce barriers to entry for those who want to partake, but may find it too complex or risky to do so. Considering the irreversibility of transactions and the absence of intermediaries, institutions looking to operate within the industry need a custody solution to protect their assets effectively, as no recourse is offered on the blockchain.
Key Differences Between Traditional and Digital Asset Custodians
While principles of custodianship are shared between traditional custody and digital asset custody providers, such as the safekeeping and servicing of assets, large differences exist due to the nature of the technology that underpins digital assets, namely distributed ledger technology (DLT). DLT introduces a new method to cryptographically store and prove ownership of digital assets. These assets are maintained by a shared network of computers (nodes), each of which maintains a synchronised record of the ledger.
By maintaining a shared ledger of transactions, there is no reliance on account-based structures. This also means that there is no need for a local register of ownership as bookkeeping is decentralised and maintained by the network, rather than a central entity that is responsible for recording changes, such as a CSD.
Challenges Associated With Self-Custody and Exchange Custody
Since the collapse of FTX, the space has felt the true consequences of counterparty risk in the most extreme terms. Over $8bn was lost by investors and traders, with claims now trading for ~20% of their original balances. When considering the custody of assets, it is vital to have a true understanding of the risks posed by exchange venues, which can be prone to vulnerabilities regardless of their size or reputation.
Self and exchange custody are convenient approaches for many retail users, however, both are inherently risky. These risks are exacerbated when dealing with institutional capital, given the complexity involved in regulated execution, as well as the size of the balances involved. Understanding the risks linked to both self-custody and deferred custody underscores the significance of partnering with regulated custodians.
Main Risks with Self or Exchange Custody:
1. Loss of Private Keys:
Compromised or lost private keys can lead to unauthorised access to funds.
2. Human Error:
Mismanagement of keys and transactional mistakes are not only easy to make but are also irreversible, leaving no option for recovery.
3.Operational Complexity:
Self-custody of assets can be complex and requires knowledge to ensure irreversible mistakes are not made.
Challenges
4. Physical Risk:
Physical solutions such as hardware wallets, or paper wallets, are prone to misplacement, damage or theft.
5. Exchange Risk:
Exchanges are a prime target for hacks and can also be prone to malicious insider behaviour.
6. Permanent Loss:
The lack of insurance coverage and regulation means that investor losses have no recourse available, making losses permanent.
Unfortunately, the digital asset sector is often a target for malicious actors looking to capitalise on the vulnerabilities inherent to self-custody and the existing security blind spots in exchange infrastructure. This reliance on such systems introduces various attack vectors that can lead to loss of funds.
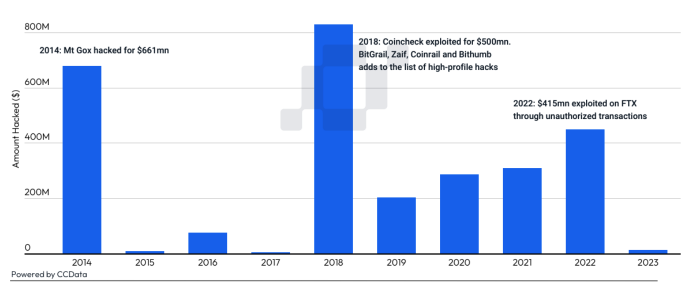
Over the years, we have seen large-scale hacking operations targeting exchanges. For example, according to Chainsec.io, there have been over $2.4bn in centralised exchange hacks in total. Some of the top exchanges, including Binance, Upbit and Bitfinex, have all experienced some type of hack or exploit. Therefore, no matter how safe an exchange appears, vulnerabilities may still exist. In some cases, it may be an insider that has privileged access, in others, it could be hackers exploiting a private key vulnerability to gain access to hot wallets.
The Mt. Gox exchange hack in 2014 is known as the most high-profile exchange hack in history. Over 850,000 BTC were stolen, worth ~ $22.4bn at current prices, leading to its bankruptcy soon after.
These challenges, in many cases, have arisen due to the way in which exchanges have been structured within the industry. Historically, exchanges have provided a wide array of services beyond the expected scope of an exchange, which can open up additional vulnerabilities and create conflicts of interest. These structures contrast Traditional Finance (TradFi) significantly, as there are limitations placed on regulated financial institutions in terms ofthe services they can offer.
As the market matures, experiences such as FTX have put pressure on the digital asset industry to de verticalise, or to separate firms into independent service providers. This has led to a reduction in counterparty risk tolerance, and some structural changes are expected, either through self regulation or external regulation by agencies such as the SEC, as seen in the case of Coinbase and Binance.
The Institutional Crypto Custody Landscape
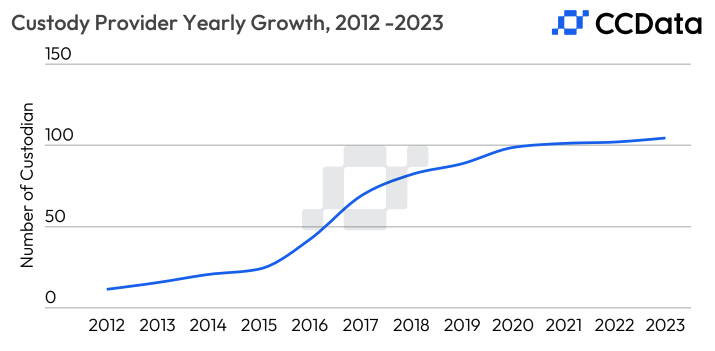
In a relatively nascent industry that is still striving for mass adoption, providing secure storage and management of digital assets for individuals, institutions, and businesses is essential. Over the last four years, the demand for custodial services has led to a surge in the number of service providers. Today, around 100 custodians are serving institutional and retail clients in the industry.
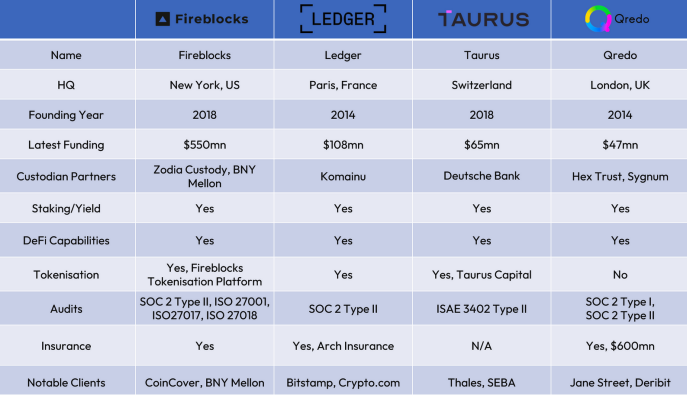
Crypto custody service providers are typically categorised into three primary groups: Custodial Technology Providers, Hybrid Custodians, and Regulated Custodians. However, as TradFi and regulated institutions continue to enter the space, with the backdrop of an evolving regulatory landscape, regulated custodians such as Zodia Custody, become increasingly important. Characteristics such as multi-jurisdictional licensing, and institutional backing, are becoming increasingly sought after to serve the needs of these institutional clients in a safe and regulated manner.
Custody Technology Providers
A custodial technology provider offers the infrastructure for clients to build their own custody solutions. Their offerings can include security infrastructure, asset transfer and settlement, and differing wallet options. Custodial Tech Providers are not responsible for storage and cannot freely move customer funds. However, they could still implement measures such as backup keys, disaster recovery mechanisms and insurance companies for the client. Since they do not have access to the customer funds, they are exempt from strict compliance laws that custodians might face.
Hybrid Custodians
A hybrid custody provider combines elements of both a custodian and a technology provider. These entities offer custodial services, primarily focusing on safeguarding client assets. However, unlike custody tech providers, they can hold users' private keys and have the authority to manage client funds when necessary. Hybrid custodians also give clients the choice of self managed custody. In this scenario, they provide technology solutions that enable clients to manage their own assets independently, maintaining control over their private keys. In this capacity, hybrid custodians operate more as a technology provider, lacking the authority to freely move client funds.
Regulated Custodians
These firms specialise in securely storing digital assets, safeguarding the client’s private keys against threats such as attempted theft and unauthorised access. A regulated custodian must comply with strict laws that may vary based on the jurisdiction in which it offers its service. Custodians can be further classified into retail custodians, institutional custodians, and custodial services using in-house and third-party custody tech.
Custodial Approaches to Security
Security Attributes
Institutional custodians employ a variety of approaches to facilitate the safe storage and accessibility of assets. However, these approaches vary depending on the type of wallet being used. In most cases, regulated custodians use a tiered wallet structure that combines hot and cold wallets to maintain high security over a significant portion of assets, while still enabling instantaneous access to execute trades when needed.
Given the need for high-quality security at an institutional level, four key attributes have arisen, according to Sepior, which underpin security operations managed by digital asset custodians.
Innovative cryptographic techniques are currently being developed to try and match all four expectations within one solution. Measures, such as Multi-Party Computation (MPC), lean on threshold cryptographic techniques which aim to minimise the trade-off between liquidity and security, meeting the four key attributes above.
A number of custodians, such as Zodia Custody, have made significant progress in optimising for this trade-off, utilising innovative measures which provides real time access to cold wallet assets, negating the need for hot or warm wallets. Furthermore, Off-Exchange Settlement has recently developed as a capital-efficient mechanism which reflects assets held with a custodian natively on exchange, removing the risks associated with exchange custody.
Wallet Types
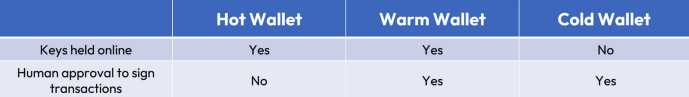
Hot Wallets are wallet solutions that are actively connected to the internet. This means the private keys, which are needed to sign transactions, remain online. Hot wallets don’t require manual intervention, as is the case with warm and cold wallets. Instead, users can transact instantaneously and without restriction. This solution mainly suits counterparties who require access to instant liquidity.
The online storage of keys in hot wallets presents an attack vector that hackers and malicious actors might exploit through techniques like hacking, phishing, and social engineering.
Warm Wallets represent a hybrid approach, incorporating elements of both hot and cold wallets. For instance, with a warm wallet, private keys are stored online, similar to a hot wallet. However, manual intervention is needed to approve a transaction before it's broadcast to the blockchain when signing transactions. Therefore, although the online attack vector still exists, the approval stage adds an additional level of control to prevent unauthorised access.
Cold Wallets maintain full offline access, meaning that private keys are never exposed to the internet. This is done by utilising ‘air gapped’ systems or Faraday cage solutions, which remove any external connection, mitigating the risk of cyber-attacks. Cold storage is seen as the safest method to store digital assets, given the absence of vulnerabilities associated with hot wallets. However, considerations must be made as to how scalable a cold wallet system is for institutional capital, as well as the trade-off that exists between speed and security. However, custodians such as Zodia Custody, who offer cold storage, may have specific infrastructure via HSM which allows for near real-time signing of transactions.
Core Security Measures:
There are three main types of security measures employed by third-party custodians which are directly related to key storage and management. Namely:
Multi-Signature,
Hardware Security Module (HSM)
Multi-Party Computation (MPC)
Multi-Signature (multi-sig): is a process which distributes transaction authorisation to more than one private key. In doing so, it removes a single point of failure. Multi-sig arrangements are also known as M-of-N arrangements, meaning that they work via a threshold system. A N number of keys are distributed, whilst a minimum M number of keys is required to reach the threshold in order to authorise a transaction. As long as this threshold is met, a proposed transaction will be executed. Multi-signature can be applied to all types of wallets, but may not be directly supported by all assets, limiting its versatility. Moreover, they are known to be difficult to scale and operationally inefficient. The thresholds are fixed by design and therefore would require a total migration to a new wallet if changes to the M of N were desired.
Multi-Party Computation (MPC): is a modern cryptographic technique that is being deployed in the digital asset custodian space. It relies on threshold cryptography to solve the trade-off between security and speed, essentially acting as a superior form of multi-signature wallet.
In MPC, the private key is split into multiple parts, called shards, and distributed among a modular network of nodes. Once created, a certain number of key shares are needed to sign and execute transactions. This ensures that no single party can control the private key and that the overall confidentiality of the keys is maintained. As MPC does not require an HSM or other physical device, it is scalable. It also requires a threshold to be met, similar to a multi-sig, which means if one key is compromised or lost, the wallet is still safe. However, unlike multi-sig, only one key is generated and then divided up. This removes the tamper-evident advantage of multi-sig and therefore reduces the overall level of accountability available via this method.
Hardware Security Modules (HSM): are physical computing appliances that are used to store sensitive cryptographic keys, which can still be used to sign transactions when needed. They have been utilised within traditional finance for over 30 years, being trusted by both banks and payment networks to effectively safeguard cryptographic keys. HSMs are also recognised under international security standards, such as the Federal Information Processing Standards (FIPS) and the National Institute of Standards and Technology (NIST). Random number generators are used to generate keys in a secure environment, which are then stored safely in cold storage within the HSM. Access is only granted to authorised personnel, or an authorised quorum, as well as being tamper-evident, leaving a clear trail of access.
In the case of digital assets, the same principles apply, but the private key being stored unlocks direct access to a wallet or funds. HSMs act as an upgraded version of a cold wallet, given their flexibility with additional security, transaction and storage mechanisms which are created at the custodian level. Some custodians, such as Zodia Custody, have managed to provide the best of both worlds by deploying an HSM based on cold-storage solutions, but with near real-time signing of transactions. The downside of HSMs is their inability to scale, due to the physical nature of the hardware modules and devices needed to sign transactions. However, these disadvantages are mainly taken on by the custodian, rather than the end-users, generally limiting their downside to users.
Key Considerations when Choosing a Custodian:
Trading Services
Custodians offer or provide access to a variety of different services in relation to trading and execution. Given that custodians are primarily serving institutional investors and entities, they have an expectation to be able to integrate seamlessly, either directly with the custodian or via API connectivity with brokers and exchanges.
From a risk perspective, institutions must be wary of counterparty risk which arises when using in-house or integrated services. For example, in-house offerings give rise to a failure of segregation of duties, which is a key risk to be considered and may enhance counterparty risk associated with the custodian itself. Similarly, integrated services are offered by vetted third parties, so clients should consider their overall risk parameters and conduct due diligence on any trading service being provided.
Off-Exchange Settlement
Off-exchange settlement is a recent innovation within institutional custody and has only been developed by a small number of custodians. However, it has the potential to revolutionise the level of counterparty risk taken on by institutional traders on their trading venues.
Off-exchange settlement (OES) allows institutional investors to hold funds safely with their custodian while having those assets reflected directly on an exchange's front end. This is achieved through a mutual partnership agreement between the custodian and the exchange, which allows for the integration of the two systems.
OES provides the benefits of utilising an exchange hot wallet, with full functionality across the exchange directly, without the assets leaving custody. This has material benefits for traders who require capital efficiency, without having to rely on the counterparty risks associated with exchange hot wallets.
Users of OES also benefit from instant, feeless off-chain deposits and withdrawals, which avoid delays due to congested networks, as well as frictionless transfers of collateral between accounts. Considering tail-risk events in the market, being able to respond with high volumes per transaction, without the risk of slow settlement, creates higher profit potential for clients looking to take advantage of volatile price movements. Moreover, it is capital efficient by avoiding liquidations and margin calls due to slow and expensive collateral transfers. As a result, institutional investors that require the use of exchange hot wallets should be focusing their attention on exchanges and custodians which offer this service.
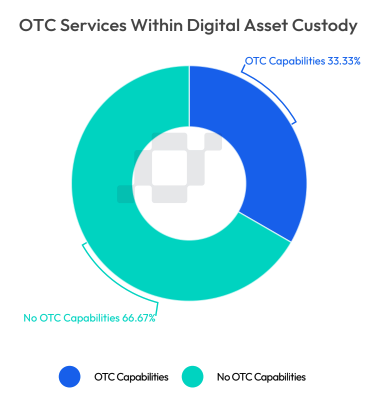
Over-the-Counter (OTC) Trading & Prime Brokerage:
OTC trading allows for trading and execution to take place without the need for an exchange. This is particularly useful when trading in larger size, or during periods of high market volatility; given that OTC trading is known to provide better execution with lower slippage in these environments. Custodians are in a strong position to offer access to OTC services, given their close relationships with OTC brokers, as well as having the infrastructure to support the execution and safe storage of assets once purchased. In some cases, custodians may have a separate entity that deals specifically with OTC or custody services, adding an additional layer of expertise and network to be utilised on the custody side.
Prime Brokerage also leverages similar relationships, with some custodians even offering prime brokerage services directly. Prime brokers essentially act as a global credit network, who aggregate liquidity providers and offer settlement in both fiat and digital assets. Custody enhances the utility of prime brokerage and OTC. All settlement and execution occurs off exchange, mitigating the risks associated with exchanges. Moreover, OTC and Prime Brokers are often regulated, which introduces added safeguards to ensure protection throughout the trading process.
Staking
Staking services have proliferated in the last few years, driven by the emergence of Proof-of Stake Layer 1s, such as ETH, which offer a yield in exchange for locking funds to assist in validating transactions on the network. Staking is a popular service for institutional capital that wants to take advantage of the yields being offered (>3%), which come as an addition to the potential price performance of their spot holdings.
As staking takes place on-chain, those who want to participate would traditionally need to self custody assets and take on the many risks associated with it. However, many custodians now offer staking services, with a wide range of offerings. The jurisdiction in which the custodian operates, and is regulated, will also have a large impact on how staking is conducted and treated for tax and investment purposes. Prospective investors should consider these elements to determine the right staking solution for them.
Analytics and Reporting
Analytics and reporting services are a necessity in the crypto ecosystem. There is a complexity involved with tracking transactions that custodians have had to solve. Similarly, there is a lot of insight to be gained through granular analytics; understanding profitability per trade, as well as slippage and volumes, can all generate insights into strategy. Moreover, having a robust reporting service removes the onus of tax reporting and tracking, which can be integrated with trading histories to generate transparent monitoring of liabilities.
Jurisdictions & Licensing:
When choosing a custody provider, one important aspect to consider is the location in which the custodian is regulated. Utilising a regulated provider has significant benefits for security and protection. However, the level of regulation to be expected is ultimately dependent on the jurisdiction in which they hold a licence.
Regulators have vastly different rules and requirements, so considering where the custodian is licensed may impact the level of security or controls one would expect. In many cases, custodians will hold multiple licences, which provides additional coverage and regulatory certainty to entities who have strict regulatory requirements. As entities scale, utilising a multi jurisdictional custodian will ensure compliance and may facilitate expansion into new locations. Some key jurisdictions and regulators are shown below.
As regulatory clarity improves, this will have a large impact on the accessibility of these markets for institutions, who have otherwise had to refrain from participating due to regulatory uncertainty. According to Fidelity, 33% of respondents to their comprehensive survey state that “Regulatory Classification Concerns of Certain Coins” is a key obstacle to investment.
The creation of notable digital asset policies in 2023, such as the case of FSMA, MiCA and VARA, will all have positive effects on the adoption of assets, by ensuring legal certainty for assets within the scope, supporting innovation and fair competition through policy, protecting consumers, institutions and market integrity, and ensuring financial stability of the ecosystem.
Audits & Accreditations:
Regulated or Qualified Custodians are required by regulatory bodies to undergo annual audits with independent, verified third-party auditors to ensure proper governance controls are in place. This prevents unauthorised access and provides transparency to clients that only those with authority to sign transactions can do so, and strict protective measures are in place.
The auditor will also need to verify that the company can access the assets, as well as audit the financial statements of the business to evaluate how a loss of assets could impact the business as a going concern. Audits also ensure that anti-money laundering (AML) and know-your customer (KYC) measures are sufficient, as well as ensuring sufficient segregation of duties, compliance, and cyber-security controls are in place.
Two key accreditations, SOC2 and ISO27001, are widely used by custodians and have both become industry standard.
SOC 2 - These accreditations, issued by the AICPA, have become an industry standard for the top institutional custodians. It is an audit opinion expressed by a chartered accountant over internal controls relating to information technology. The scope is assessed against the Trust Services Criteria (TSC) and demonstrates compliance to a set of controls which address security, availability, integrity, confidentiality and privacy. It can be integrated with other controls such as Cobit or ISO/IEC 27001, enhancing trust in the custodian. It provides strong insight into key risk and governance controls, whilst solidifying trust.
AICPA also issues a SOC 1, which custodians may also apply for, but that criteria is focused on financial controls and may be less vital in the case of due diligence for a custodian, given the main concern surrounds IT security controls.
ISO27001 - Backed by the International Standards Organisation (ISO), achieving an ISO27001 accreditation shows adherence towards information security protocols, as judged by the ISO.
According to ISO, It means custody providers have put in place a system to manage risks related to the security of data owned and handled by the company, and that this system respects all best practices and principles enshrined in the International Standard. This standard is globally recognised and applies to many industries, but has been used as a good foundational measure by custodians to demonstrate willingness to comply with recognised standards for security.
Insurance
Considering the level of insurance coverage offered by a custodian is vital, as it will form part of all due diligence processes associated with digital asset investment and storage. Having a high level of coverage is important for institutions to feel comfortable engaging with the space. Regardless of the security measures that are in place, insurance will always be necessary to mitigate any counterparty risks with the custodians themselves.
The insurance cover required will depend upon the custodian, and what type of services they offer. Qualified Custodians are likely to have a higher insurance coverage and therefore more protections. In most cases, insurance coverage includes cold storage insurance and crime insurance. However, other types of coverage include misuse where the custodian holds the keys, theft, collusion, transfer, and errors & omissions.
The discrepancy of coverage between hot and cold wallets needs to be considered by potential investors, as depending on the focus of their work, one may be more applicable. There may also be gaps in coverage throughout the lifecycle of using a custodian, as well as an evolution in the type of coverage that is required as a business potentially scales and engages in different parts of the ecosystem, such as staking, OTC/PB trading, DeFi, asset transfers etc.
Users of Custodial Services
Users of custodial services tend to fall into two main categories: investors and infrastructure. Within investors, we can consider high-frequency and low-frequency investors, with the greatest variation based on how regularly they are executing trades. Within infrastructure, we have highlighted two key market segments, namely exchanges, and digital asset management product issuers.
Investors - High Frequency:
High-frequency investors, such as family offices, hedge funds, algorithmic traders, market makers and high-net-worth individuals, are all examples of high-frequency investors, driving their overarching requirement for instant access to liquidity. Therefore, some portion of their active trading portfolio will need to exist on a hot wallet.
This segment would benefit from services such as an OES, which allows these firms to trade derivatives natively on an exchange with a full product suite available to them. High-frequency traders and market makers tend to trade in significant volumes, and therefore over-exposure to hot wallets could be detrimental to their risk-reward profile.
Investors - Low Frequency:
Low-frequency investors, such as pension funds and venture capitalists, tend to have longer time horizons and rebalance portfolios on an infrequent basis. As a result, their priority would align with security, over speed, with all assets being held in cold storage until a rebalance or vesting cliff ends.
Infrastructure - Exchanges
Exchanges form a core part of digital asset infrastructure and have specific needs for engaging custodians. Exchanges have the option to store client assets in either hot or cold storage. While hot storage facilitates immediate client deposits and withdrawals, cold storage utilises specialised hardware and technology, offering greater security. Therefore, most exchanges recommend and often store the majority of their assets in cold storage.
Following the collapse of FTX and the consequent lawsuits against Coinbase, Binance and others, the need for the independent custodianship of assets and private keys has been exacerbated. Since regulated custodians have a fiduciary duty to hold its clients funds in segregated accounts while meeting stringent regulatory standards and frequent audit requirements, they are deemed the safest method of safeguarding clients using a third party. Moreover, most custodians provide insurance coverage to exchanges against events of theft, hacks, and misuse.
Infrastructure - Digital Asset Investment Product Providers
Issuers of digital asset products may require the use of a custodian. For example, trust products, such as Grayscale’s Bitcoin Trust, would require a qualified/regulated custodian to store the Bitcoin in cold storage. Similarly, when a Bitcoin Spot ETF is approved, the issuer will also need to custody the assets with a regulated or qualified custodian, as spot ETFs require possession of the underlying asset.
Digital Asset Custody: Innovations & Trends
The digital asset space is nascent, but ever-evolving. The custodial landscape will have to adapt to new innovations and trends over time, especially as the industry is very sensitive to technological innovation. Considering the wallet growth taking place within Bitcoin and Ethereum alone, there is a clear trend towards usage and adoption, and custodians will need to be quick to respond to innovative changes within the industry to facilitate the institutionalisation of digital assets.
The Rise of Staking
Staking has become a key mechanism of the industry, driven by the proliferation of Layer 1s utilising Proof-of-Stake. Layer 1s refer to tokens such as ETH or SOL who operate their own blockchain networks. Since the end of August, over $20bn has been staked in decentralised protocols, highlighting the significant and material level of TVL entering staking contracts.
However, as the industry matures, staking services are likely to become further dominated by institutional capital. Therefore, to encourage safe participation in network validation and yield generation, custodians will be required to assist operationally to enable non-native investors to take advantage of these opportunities.
Tokenisation and Real-World Assets (RWA):
Tokenised assets are an emerging trend within the space. In 2023 alone, total-value-locked (TVL) in RWA protocols has increased tenfold since the start of the year, with investors utilising this technology on-chain to invest in alternative asset classes. Although in its infancy, the concept of tokenisation can be applied to many assets, including equities, fixed income, real estate, commodities, private markets, carbon credits, art & media among others. Stablecoins are also considered tokenisation of the dollar, which has brought many capital-efficient benefits to transferring value.
According to Citi's GPS report, they expect tokenisation to grow by a factor of over 80x in private markets, and reach up to $4tn in value by 2030. They also forecast that $1tn of the repo, securities financing and collateral market to be tokenised by 2030. The custodian's role in tokenisation is crucial, with responsibilities varying based on the assets in custody and the engaged service. However, generally speaking, custodians take on the following responsibilities in the case of tokenised assets:
Asset Management: Managing the issuance, distribution and redemption of tokenised assets on behalf of the issuer, or investor, and maintaining records of ownership.
Compliance and Regulation: Custodians ensure compliance with regulatory requirements and conduct required KYC and AML measures.
Liquidity Enhancements: Custodians can play a vital role in regard to facilitating the buying and selling of tokenised assets by ensuring access to liquidity pools.
Security and Transparency: Custodians use their security standards and on-chain expertise to securely manage assets while maintaining transparency and keeping records.
In many cases, tokenised assets are already regulated in traditional finance. By bringing them on-chain, investors will be required to custody these regulated tokens with custodians who are already regulated. Some custodians have already implemented a tokenisation strategy, partnering with on-chain protocols who issue tokenised products, as well as traditional finance players to bridge the gap towards on-chain assets.
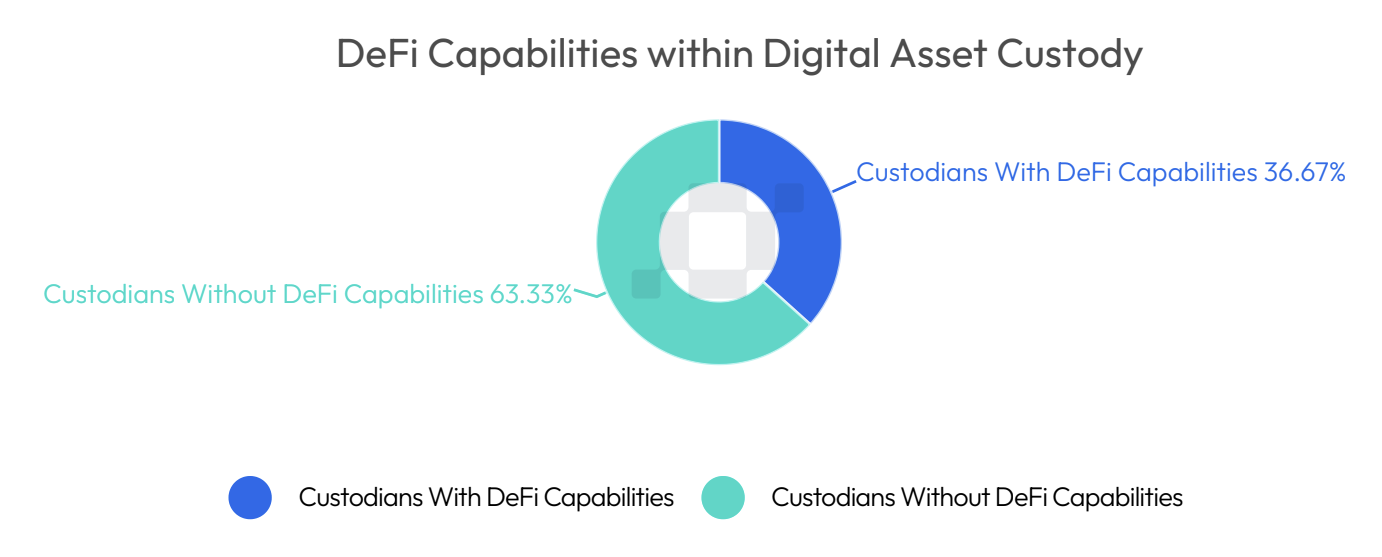
DeFi & Interoperability:
DeFi (Decentralised Finance) is another area of the digital asset sector that has seen exponential growth, offering lending and borrowing in a non-custodial setting on the blockchain. This growth was shadowed by a series of exploits, making institutional adoption challenging due to the associated risks of directly using these platforms.
Institutional custody providers allow institutions to benefit from the opportunities and yields offered by DeFi protocols while still maintaining the security and regulatory compliance of their assets. For example, through partnerships with certain protocols, some custodians offer direct and secure access to DeFi right from their custody platform. Many exploits have occurred due to the vulnerabilities associated with bridges, which are key mechanisms that enhance interoperability between different blockchains. Over the past few years, bridges have shown their innate weakness, with two bridges alone, the Ronin Bridge and the Horizon bridge, accounting for $625mn and $100mn in losses respectively.
Institutional Products:
While retail investor participation has declined, evident from the high derivatives-to-spot volume market shares (currently at 76%) and consistently falling prices of tokens favoured by retail investors, one segment of the industry remains resilient: Digital Asset Exchange-Traded Products, including ETFs and Trusts. Digital asset investment products have maintained strong AUMs this year, with total aggregated AUMs exceeding $35bn in August.
The recent spot BTC ETF filing by Blackrock, the largest asset manager in the world, as well as recent positive developments related to Grayscale’s legal appeal to convert to a Spot BTC ETF, have solidified the appetite of institutional investors to participate in the space via regulated instruments. The existence of Futures ETFs have allowed institutional traders to speculate on digital assets, however, the approval for a Spot ETF in the US is likely to change the landscape for the sector. Further improvements to institutional sentiment have come from recent legal wins by Ripple, whereby a judge ruled that XRP was not a security when made available to the general public. This win has improved the chances of digital assets being deemed non-securities in the US, which directly impacts the accessibility of these assets to institutions that are bound by SEC regulations. It also widens the scope for the creation of new investment products centered around Altcoins, such as Solana, Ripple and Cardano.
Concluding Thoughts
The institutional landscape within digital assets is evolving and custodians need to be responsive in their offerings. As counterparty risk remains one of the largest barriers to entry, institutional custodians have an opportunity to drive adoption by mitigating these risks for investment and asset managers.
Institutions looking for a custody provider should engage the services of a custodian that offers innovative cryptographic solutions, such as HSM or OES, like Zodia Custody. Using these services significantly reduces counterparty risk and provides confidence and safety to institutions. Additionally, insurance coverage and operational support can reduce the complexities of navigating an immutable distributed ledger, and provide recourse if needed.
Custodians are also developing tertiary services, mainly relating to trading, which could replace the use of exchanges for many targeted market segments. The introduction and facilitation of trading via API through OTC and Prime Brokerage reduces the need for engaging additional counterparties, who all possess additional inherent risk factors. However, in taking these steps, custodians need to be aware of the additional complexities and risk factors associated with their partners, to avoid the many drawbacks seen in the lack of segregation of duties witnessed in key centralised exchanges. Furthermore, as the industry continues to innovate, through DeFi expansion and the Tokenisation of RWA, custodians who provide coverage of these integral services may facilitate the growth expected in these sectors.
As the regulatory landscape becomes more certain, with the introduction of comprehensive virtual asset policy, such as MiCA, FSMA, and VARA, it is likely to spur adoption, by reducing the regulatory risk associated with investing and building in this nascent space. As regulatory frameworks continue to evolve, institutions should seek custodians who can actively adapt to these changes in a fluid, and compliant manner.
About CCData:
CCData is an FCA-authorised benchmark administrator and global leader in digital asset data, providing institutional-grade digital asset data and settlement indices. By aggregating and analysing tick data from globally recognised exchanges and seamlessly integrating multiple datasets, CCData provides a comprehensive and granular overview of the market across trade, derivatives, order book, historical, social and blockchain data.
CCData Research:
CCData's suite of complementary research reports deliver high-quality, trusted and unbiased data-driven analysis into the latest trends and narratives within the sector. Our award winning research team is trusted by a highly institutional audience and is regularly featured in leading traditional and crypto press, from Bloomberg and the Financial Times, to Coindesk and more.
Data for this report was collected up to the 30th September 2023.